Schwachstelle kann geschlossen werden
Microsoft hat nachgearbeitet und am 14.September einen weiteren Patch veröffentlicht, der die Sicherheitsanfälligkeit CVE-2021-36958 beheben soll.
PrintNightmare Patch verfügbar
PrintNightmare Patch 2 September 2021 verfügbar für folgende Systeme:
| Produkt | Schweregrad | Article | Download | Details |
|---|---|---|---|---|
| Windows Server 2012 R2 (Server Core installation) | Important | 5005613 | Monthly Rollup | CVE-2021-36958 |
| Windows Server 2012 R2 (Server Core installation) | Important | 5005627 | Security Only | CVE-2021-36958 |
| Windows Server 2012 R2 | Important | 5005613 | Monthly Rollup | CVE-2021-36958 |
| Windows Server 2012 R2 | Important | 5005627 | Security Only | CVE-2021-36958 |
| Windows Server 2012 (Server Core installation) | Important | 5005623 | Monthly Rollup | CVE-2021-36958 |
| Windows Server 2012 (Server Core installation) | Important | 5005607 | Security Only | CVE-2021-36958 |
| Windows Server 2012 | Important | 5005623 | Monthly Rollup | CVE-2021-36958 |
| Windows Server 2012 | Important | 5005607 | Security Only | CVE-2021-36958 |
| Windows Server 2008 R2 for x64-based Systems Service Pack 1 (Server Core installation) | Important | 5005633 | Monthly Rollup | CVE-2021-36958 |
| Windows Server 2008 R2 for x64-based Systems Service Pack 1 (Server Core installation) | Important | 5005615 | Security Only | CVE-2021-36958 |
| Windows Server 2008 R2 for x64-based Systems Service Pack 1 | Important | 5005633 | Monthly Rollup | CVE-2021-36958 |
| Windows Server 2008 R2 for x64-based Systems Service Pack 1 | Important | 5005615 | Security Only | CVE-2021-36958 |
| Windows Server 2008 for x64-based Systems Service Pack 2 (Server Core installation) | Important | 5005606 | Monthly Rollup | CVE-2021-36958 |
| Windows Server 2008 for x64-based Systems Service Pack 2 (Server Core installation) | Important | 5005618 | Security Only | CVE-2021-36958 |
| Windows Server 2008 for x64-based Systems Service Pack 2 | Important | 5005606 | Monthly Rollup | CVE-2021-36958 |
| Windows Server 2008 for x64-based Systems Service Pack 2 | Important | 5005618 | Security Only | CVE-2021-36958 |
| Windows Server 2008 for 32-bit Systems Service Pack 2 (Server Core installation) | Important | 5005606 | Monthly Rollup | CVE-2021-36958 |
| Windows Server 2008 for 32-bit Systems Service Pack 2 (Server Core installation) | Important | 5005618 | Security Only | CVE-2021-36958 |
| Windows Server 2008 for 32-bit Systems Service Pack 2 | Important | 5005606 | Monthly Rollup | CVE-2021-36958 |
| Windows Server 2008 for 32-bit Systems Service Pack 2 | Important | 5005618 | Security Only | CVE-2021-36958 |
| Windows RT 8.1 | Important | 5005613 | Monthly Rollup | CVE-2021-36958 |
| Windows 8.1 for x64-based systems | Important | 5005613 | Monthly Rollup | CVE-2021-36958 |
| Windows 8.1 for x64-based systems | Important | 5005627 | Security Only | CVE-2021-36958 |
| Windows 8.1 for 32-bit systems | Important | 5005613 | Monthly Rollup | CVE-2021-36958 |
| Windows 8.1 for 32-bit systems | Important | 5005627 | Security Only | CVE-2021-36958 |
| Windows 7 for x64-based Systems Service Pack 1 | Important | 5005633 | Monthly Rollup | CVE-2021-36958 |
| Windows 7 for x64-based Systems Service Pack 1 | Important | 5005615 | Security Only | CVE-2021-36958 |
| Windows 7 for 32-bit Systems Service Pack 1 | Important | 5005633 | Monthly Rollup | CVE-2021-36958 |
| Windows 7 for 32-bit Systems Service Pack 1 | Important | 5005615 | Security Only | CVE-2021-36958 |
| Windows Server 2016 (Server Core installation) | Important | 5005573 | Security Update | CVE-2021-36958 |
| Windows Server 2016 | Important | 5005573 | Security Update | CVE-2021-36958 |
| Windows 10 Version 1607 for x64-based Systems | Important | 5005573 | Security Update | CVE-2021-36958 |
| Windows 10 Version 1607 for 32-bit Systems | Important | 5005573 | Security Update | CVE-2021-36958 |
| Windows 10 for x64-based Systems | Important | 5005569 | Security Update | CVE-2021-36958 |
| Windows 10 for 32-bit Systems | Important | 5005569 | Security Update | CVE-2021-36958 |
| Windows Server, version 20H2 (Server Core Installation) | Important | 5005565 | Security Update | CVE-2021-36958 |
| Windows 10 Version 20H2 for ARM64-based Systems | Important | 5005565 | Security Update | CVE-2021-36958 |
| Windows 10 Version 20H2 for 32-bit Systems | Important | 5005565 | Security Update | CVE-2021-36958 |
| Windows 10 Version 20H2 for x64-based Systems | Important | 5005565 | Security Update | CVE-2021-36958 |
| Windows Server, version 2004 (Server Core installation) | Important | 5005565 | Security Update | CVE-2021-36958 |
| Windows 10 Version 2004 for x64-based Systems | Important | 5005565 | Security Update | CVE-2021-36958 |
| Windows 10 Version 2004 for ARM64-based Systems | Important | 5005565 | Security Update | CVE-2021-36958 |
| Windows 10 Version 2004 for 32-bit Systems | Important | 5005565 | Security Update | CVE-2021-36958 |
| Windows 10 Version 21H1 for 32-bit Systems | Important | 5005565 | Security Update | CVE-2021-36958 |
| Windows 10 Version 21H1 for ARM64-based Systems | Important | 5005565 | Security Update | CVE-2021-36958 |
| Windows 10 Version 21H1 for x64-based Systems | Important | 5005565 | Security Update | CVE-2021-36958 |
| Windows 10 Version 1909 for ARM64-based Systems | Important | 5005566 | Security Update | CVE-2021-36958 |
| Windows 10 Version 1909 for x64-based Systems | Important | 5005566 | Security Update | CVE-2021-36958 |
| Windows 10 Version 1909 for 32-bit Systems | Important | 5005566 | Security Update | CVE-2021-36958 |
| Windows Server 2019 (Server Core installation) | Important | 5005568 | Security Update | CVE-2021-36958 |
| Windows Server 2019 | Important | 5005568 | Security Update | CVE-2021-36958 |
| Windows 10 Version 1809 for ARM64-based Systems | Important | 5005568 | Security Update | CVE-2021-36958 |
| Windows 10 Version 1809 for x64-based Systems | Important | 5005568 | Security Update | CVE-2021-36958 |
| Windows 10 Version 1809 for 32-bit Systems | Important | 5005568 | Security Update | CVE-2021-36958 |
Security Updates 2021-09-17 Patch 2 Print Nightmare
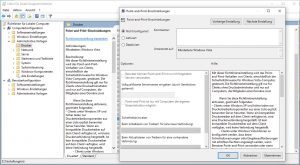
Der Patch 1 schützte nur, wenn folgende Richtlinie nicht konfiguriert wurde.
Diese Registry-Schlüssel, wenn vorhanden müssen den Wert 0 = aufweisen. Sind die Schlüssel nicht vorhanden schützt der Patch ebenfalls!
HKEY_LOCAL_MACHINE\SOFTWARE\Policies\Microsoft\Windows NT\Printers\PointAndPrint
DWORD-Wert (32-Bit)
NoWarningNoElevationOnInstall = 0
UpdatePromptSettings = 0
Stehen die Werte auf = 1 weichen diese Einstellung vom Standard ab, und der Patch schützt nicht!