Schwache TLS Cipher Suites abschalten
Disable all weak TLS Cipher Suites – Schwache Verschlüsselungssammlungen sind ein Grund dafür, das gewisse Services von einem Webbrowser verweigert werden können.
SSL/TLS sind Protokolle, die eine verschlüsselte Verbindung zwischen zwei Teilnehmern garantiert. SSL/TLS unterstützt dabei die verschiedensten Algorithmen, wobei einige bereits als schwach gelten, da entweder der Algorithmus Schwächen aufweist oder die verwendeten Schlüssel zu kurz sind.
Disable all weak TLS Cipher Suites
Um die Möglichkeit einer unsicheren Verbindung nicht aufkommen zu lassen, ist es empfehlenswert, sämtliche Algorithmen, die nur eine Pseudo-Verschlüsselung oder eine unzureichende Verschlüsselung bieten, zu deaktivieren.
Das nachfolgende Skript enthält eine Liste schwacher Cipher Suites die nach Ausführung des Skripts deaktivert wären.
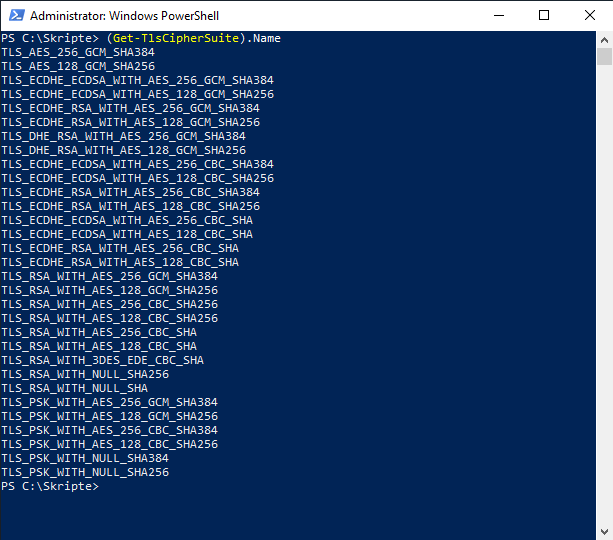
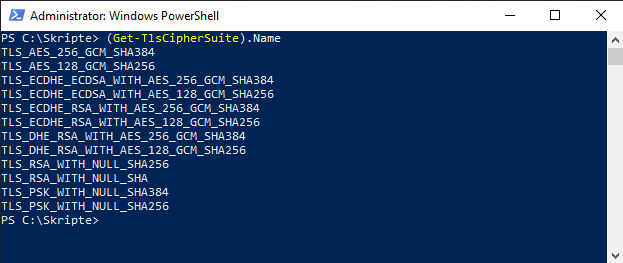
Die Cipher Suiten lassen sich vorher und nachher mit diesem Befehl auslesen.
# (Get-TlsCipherSuite).Name
$WeakCiphers =
@(
“TLS_DH_DSS_WITH_AES_256_CBC_SHA”
“TLS_DH_DSS_WITH_AES_256_CBC_SHA256”
“TLS_DH_DSS_WITH_CAMELLIA_128_CBC_SHA”
“TLS_DH_DSS_WITH_CAMELLIA_128_CBC_SHA256”
“TLS_DH_DSS_WITH_CAMELLIA_256_CBC_SHA”
“TLS_DH_DSS_WITH_CAMELLIA_256_CBC_SHA256”
“TLS_DH_DSS_WITH_SEED_CBC_SHA”
“TLS_DHE_DSS_WITH_AES_256_CBC_SHA”
“TLS_DHE_DSS_WITH_AES_256_CBC_SHA256”
“TLS_DHE_DSS_WITH_SEED_CBC_SHA”
“TLS_DH_RSA_WITH_CAMELLIA_128_CBC_SHA”
“TLS_DH_RSA_WITH_CAMELLIA_256_CBC_SHA”
“TLS_ECDHE_ECDSA_WITH_AES_128_CBC_SHA256”
“TLS_ECDHE_RSA_WITH_ARIA_256_CBC_SHA384”
“TLS_ECDH_RSA_WITH_3DES_EDE_CBC_SHA”
“TLS_ECDH_RSA_WITH_AES_128_CBC_SHA”
“TLS_ECDH_RSA_WITH_ARIA_128_CBC_SHA256”
“TLS_KRB5_WITH_3DES_EDE_CBC_SHA”
“TLS_RSA_PSK_WITH_3DES_EDE_CBC_SHA”
“TLS_RSA_PSK_WITH_AES_128_CBC_SHA”
“TLS_RSA_PSK_WITH_AES_256_CBC_SHA”
“TLS_RSA_WITH_3DES_EDE_CBC_SHA”
“TLS_RSA_WITH_AES_128_CBC_SHA256”
“TLS_RSA_WITH_AES_128_GCM_SHA256”
“TLS_RSA_WITH_AES_256_CBC_SHA”
“TLS_RSA_WITH_AES_256_GCM_SHA384”
“TLS_DH_DSS_WITH_3DES_EDE_CBC_SHA”
“TLS_DH_DSS_WITH_AES_128_CBC_SHA”
“TLS_DH_DSS_WITH_AES_128_CBC_SHA256”
“TLS_DH_DSS_WITH_AES_128_GCM_SHA256”
“TLS_DHE_PSK_WITH_ARIA_256_GCM_SHA384”
“TLS_DHE_PSK_WITH_CAMELLIA_256_GCM_SHA384”
“TLS_DH_RSA_WITH_ARIA_128_CBC_SHA256”
“TLS_DH_RSA_WITH_ARIA_256_CBC_SHA384”
“TLS_DH_RSA_WITH_CAMELLIA_128_CBC_SHA256”
“TLS_DH_RSA_WITH_CAMELLIA_256_CBC_SHA256”
“TLS_DH_RSA_WITH_SEED_CBC_SHA”
“TLS_ECDH_ECDSA_WITH_3DES_EDE_CBC_SHA”
“TLS_ECDH_ECDSA_WITH_AES_128_CBC_SHA”
“TLS_ECDH_ECDSA_WITH_AES_128_CBC_SHA256”
“TLS_ECDH_ECDSA_WITH_AES_128_GCM_SHA256”
“TLS_ECDHE_ECDSA_WITH_AES_256_CBC_SHA”
“TLS_ECDHE_ECDSA_WITH_ARIA_256_CBC_SHA384”
“TLS_ECDHE_PSK_WITH_3DES_EDE_CBC_SHA”
“TLS_PSK_DHE_WITH_AES_128_CCM_8”
“TLS_PSK_DHE_WITH_AES_256_CCM_8”
“TLS_PSK_WITH_3DES_EDE_CBC_SHA”
“TLS_PSK_WITH_AES_128_CBC_SHA”
“TLS_PSK_WITH_AES_128_CBC_SHA256”
“TLS_PSK_WITH_AES_128_CCM”
“TLS_PSK_WITH_AES_128_GCM_SHA256”
“TLS_RSA_PSK_WITH_AES_128_GCM_SHA256”
“TLS_RSA_PSK_WITH_AES_256_CBC_SHA384”
“TLS_RSA_PSK_WITH_AES_256_GCM_SHA384”
“TLS_RSA_WITH_ARIA_128_CBC_SHA256”
“TLS_RSA_WITH_ARIA_256_CBC_SHA384”
“TLS_RSA_WITH_CAMELLIA_128_CBC_SHA”
“TLS_RSA_WITH_CAMELLIA_128_CBC_SHA256”
“TLS_RSA_WITH_CAMELLIA_256_CBC_SHA”
“TLS_RSA_WITH_CAMELLIA_256_CBC_SHA256”
“TLS_RSA_WITH_IDEA_CBC_SHA”
“TLS_RSA_WITH_SEED_CBC_SHA”
“TLS_DH_DSS_WITH_ARIA_128_CBC_SHA256”
“TLS_DHE_DSS_WITH_AES_128_CBC_SHA”
“TLS_DHE_DSS_WITH_ARIA_128_CBC_SHA256”
“TLS_DHE_PSK_WITH_3DES_EDE_CBC_SHA”
“TLS_DHE_PSK_WITH_ARIA_256_CBC_SHA384”
“TLS_DH_DSS_WITH_ARIA_256_CBC_SHA384”
“TLS_DH_DSS_WITH_ARIA_256_GCM_SHA384”
“TLS_DH_DSS_WITH_CAMELLIA_256_GCM_SHA384”
“TLS_DHE_DSS_WITH_ARIA_128_GCM_SHA256”
“TLS_DHE_DSS_WITH_ARIA_256_CBC_SHA384”
“TLS_DHE_DSS_WITH_ARIA_256_GCM_SHA384”
“TLS_DHE_PSK_WITH_CAMELLIA_128_CBC_SHA256”
“TLS_DHE_PSK_WITH_CAMELLIA_128_GCM_SHA256”
“TLS_DHE_PSK_WITH_CHACHA20_POLY1305_SHA256”
“TLS_DH_RSA_WITH_ARIA_128_GCM_SHA256”
“TLS_DH_RSA_WITH_ARIA_256_GCM_SHA384”
“TLS_ECDH_ECDSA_WITH_AES_256_GCM_SHA384”
“TLS_ECDH_ECDSA_WITH_ARIA_128_CBC_SHA256”
“TLS_ECDH_ECDSA_WITH_ARIA_256_CBC_SHA384”
“TLS_ECDH_ECDSA_WITH_ARIA_256_GCM_SHA384”
“TLS_ECDH_ECDSA_WITH_CAMELLIA_128_CBC_SHA256”
“TLS_ECDH_ECDSA_WITH_CAMELLIA_256_CBC_SHA384”
“TLS_ECDHE_ECDSA_WITH_CAMELLIA_256_CBC_SHA384”
“TLS_ECDHE_PSK_WITH_AES_128_CBC_SHA”
“TLS_ECDHE_PSK_WITH_AES_128_CBC_SHA256”
“TLS_ECDHE_PSK_WITH_ARIA_128_CBC_SHA256”
“TLS_ECDHE_PSK_WITH_ARIA_256_CBC_SHA384”
“TLS_ECDHE_RSA_WITH_AES_128_CBC_SHA256”
“TLS_ECDH_RSA_WITH_AES_128_CBC_SHA256”
“TLS_PSK_WITH_CHACHA20_POLY1305_SHA256”
“TLS_RSA_WITH_AES_128_CCM”
“TLS_RSA_WITH_ARIA_128_GCM_SHA256”
“TLS_RSA_WITH_ARIA_256_GCM_SHA384”
“TLS_RSA_WITH_CAMELLIA_128_GCM_SHA256”
“TLS_RSA_WITH_CAMELLIA_256_GCM_SHA384”
“TLS_SRP_SHA_DSS_WITH_AES_128_CBC_SHA”
“TLS_SRP_SHA_DSS_WITH_AES_256_CBC_SHA”
“TLS_SRP_SHA_RSA_WITH_3DES_EDE_CBC_SHA”
“TLS_SRP_SHA_RSA_WITH_AES_128_CBC_SHA”
“TLS_SRP_SHA_RSA_WITH_AES_256_CBC_SHA”
“TLS_SRP_SHA_WITH_3DES_EDE_CBC_SHA”
“TLS_SRP_SHA_WITH_AES_128_CBC_SHA”
“TLS_SRP_SHA_WITH_AES_256_CBC_SHA”
“TLS_DH_DSS_WITH_AES_256_GCM_SHA384”
“TLS_DH_DSS_WITH_ARIA_128_GCM_SHA256”
“TLS_DHE_DSS_WITH_AES_128_CBC_SHA256”
“TLS_DHE_DSS_WITH_AES_128_GCM_SHA256”
“TLS_DHE_DSS_WITH_AES_256_GCM_SHA384”
“TLS_DHE_DSS_WITH_CAMELLIA_128_GCM_SHA256”
“TLS_DHE_PSK_WITH_AES_128_CCM”
“TLS_DHE_RSA_WITH_3DES_EDE_CBC_SHA”
“TLS_DHE_RSA_WITH_AES_128_CBC_SHA”
“TLS_DHE_RSA_WITH_AES_128_CBC_SHA256”
“TLS_DHE_RSA_WITH_AES_128_CCM”
“TLS_DH_RSA_WITH_AES_256_GCM_SHA384”
“TLS_DH_RSA_WITH_CAMELLIA_128_GCM_SHA256”
“TLS_DH_RSA_WITH_CAMELLIA_256_GCM_SHA384”
“TLS_ECDHE_ECDSA_WITH_CAMELLIA_128_CBC_SHA256”
“TLS_ECDHE_PSK_WITH_AES_256_CBC_SHA”
“TLS_ECDHE_PSK_WITH_AES_256_CBC_SHA384”
“TLS_ECDH_RSA_WITH_AES_256_CBC_SHA384”
“TLS_KRB5_WITH_IDEA_CBC_SHA”
“TLS_PSK_WITH_AES_128_CCM_8”
“TLS_PSK_WITH_AES_256_CCM_8”
“TLS_RSA_WITH_AES_128_CCM_8”
“TLS_RSA_WITH_AES_256_CBC_SHA256”
“TLS_RSA_WITH_AES_256_CCM”
“TLS_RSA_WITH_AES_256_CCM_8”
“TLS_DHE_DSS_WITH_3DES_EDE_CBC_SHA”
“TLS_PSK_WITH_CAMELLIA_256_CBC_SHA384”
“TLS_PSK_WITH_CAMELLIA_256_GCM_SHA384”
“TLS_RSA_PSK_WITH_AES_128_CBC_SHA256”
“TLS_RSA_WITH_AES_128_CBC_SHA”
“TLS_DHE_DSS_WITH_CAMELLIA_256_CBC_SHA”
“TLS_DHE_DSS_WITH_CAMELLIA_256_CBC_SHA256”
“TLS_DHE_DSS_WITH_CAMELLIA_256_GCM_SHA384”
“TLS_DHE_PSK_WITH_AES_128_CBC_SHA”
“TLS_DHE_PSK_WITH_AES_128_CBC_SHA256”
“TLS_DHE_PSK_WITH_AES_128_GCM_SHA256”
“TLS_DHE_PSK_WITH_AES_256_CBC_SHA”
“TLS_DHE_PSK_WITH_AES_256_CBC_SHA384”
“TLS_DHE_PSK_WITH_AES_256_CCM”
“TLS_DHE_PSK_WITH_AES_256_GCM_SHA384”
“TLS_DHE_PSK_WITH_ARIA_128_CBC_SHA256”
“TLS_DHE_PSK_WITH_ARIA_128_GCM_SHA256”
“TLS_DHE_RSA_WITH_AES_256_GCM_SHA384”
“TLS_DHE_RSA_WITH_ARIA_256_GCM_SHA384”
“TLS_DHE_RSA_WITH_CAMELLIA_128_CBC_SHA”
“TLS_DHE_RSA_WITH_CAMELLIA_128_GCM_SHA256”
“TLS_DHE_RSA_WITH_CAMELLIA_256_CBC_SHA”
“TLS_DHE_RSA_WITH_SEED_CBC_SHA”
“TLS_ECDH_ECDSA_WITH_AES_256_CBC_SHA”
“TLS_ECDH_ECDSA_WITH_AES_256_CBC_SHA384”
“TLS_ECDH_ECDSA_WITH_CAMELLIA_256_GCM_SHA384”
“TLS_ECDHE_ECDSA_WITH_3DES_EDE_CBC_SHA”
“TLS_ECDHE_ECDSA_WITH_AES_128_CBC_SHA”
“TLS_ECDHE_ECDSA_WITH_AES_256_CBC_SHA384”
“TLS_ECDHE_ECDSA_WITH_ARIA_128_CBC_SHA256”
“TLS_ECDHE_RSA_WITH_3DES_EDE_CBC_SHA”
“TLS_ECDHE_RSA_WITH_AES_256_CBC_SHA384”
“TLS_ECDHE_RSA_WITH_CAMELLIA_128_CBC_SHA256”
“TLS_RSA_PSK_WITH_ARIA_128_CBC_SHA256”
“TLS_RSA_PSK_WITH_ARIA_128_GCM_SHA256”
“TLS_RSA_PSK_WITH_ARIA_256_CBC_SHA384”
“TLS_RSA_PSK_WITH_ARIA_256_GCM_SHA384”
“TLS_RSA_PSK_WITH_CAMELLIA_128_CBC_SHA256”
“TLS_RSA_PSK_WITH_CAMELLIA_128_GCM_SHA256”
“TLS_RSA_PSK_WITH_CAMELLIA_256_GCM_SHA384”
“TLS_DH_DSS_WITH_CAMELLIA_128_GCM_SHA256”
“TLS_DHE_DSS_WITH_CAMELLIA_128_CBC_SHA256”
“TLS_DHE_RSA_WITH_ARIA_256_CBC_SHA384”
“TLS_DHE_RSA_WITH_CAMELLIA_256_GCM_SHA384”
“TLS_DHE_RSA_WITH_CHACHA20_POLY1305_SHA256”
“TLS_DH_RSA_WITH_3DES_EDE_CBC_SHA”
“TLS_DH_RSA_WITH_AES_128_CBC_SHA”
“TLS_DH_RSA_WITH_AES_128_GCM_SHA256”
“TLS_DH_RSA_WITH_AES_256_CBC_SHA”
“TLS_DH_RSA_WITH_AES_256_CBC_SHA256”
“TLS_ECDH_ECDSA_WITH_ARIA_128_GCM_SHA256”
“TLS_ECDH_ECDSA_WITH_CAMELLIA_128_GCM_SHA256”
“TLS_ECDHE_PSK_WITH_CAMELLIA_128_CBC_SHA256”
“TLS_ECDHE_PSK_WITH_CAMELLIA_256_CBC_SHA384”
“TLS_ECDHE_RSA_WITH_AES_128_CBC_SHA”
“TLS_ECDHE_RSA_WITH_AES_256_CBC_SHA”
“TLS_ECDHE_RSA_WITH_ARIA_128_CBC_SHA256”
“TLS_ECDH_RSA_WITH_AES_128_GCM_SHA256”
“TLS_ECDH_RSA_WITH_AES_256_CBC_SHA”
“TLS_ECDH_RSA_WITH_AES_256_GCM_SHA384”
“TLS_ECDH_RSA_WITH_ARIA_128_GCM_SHA256”
“TLS_ECDH_RSA_WITH_ARIA_256_CBC_SHA384”
“TLS_ECDH_RSA_WITH_ARIA_256_GCM_SHA384”
“TLS_ECDH_RSA_WITH_CAMELLIA_128_CBC_SHA256”
“TLS_ECDH_RSA_WITH_CAMELLIA_128_GCM_SHA256”
“TLS_ECDH_RSA_WITH_CAMELLIA_256_CBC_SHA384”
“TLS_ECDH_RSA_WITH_CAMELLIA_256_GCM_SHA384”
“TLS_PSK_WITH_AES_256_CBC_SHA”
“TLS_PSK_WITH_AES_256_CBC_SHA384”
“TLS_PSK_WITH_AES_256_CCM”
“TLS_PSK_WITH_AES_256_GCM_SHA384”
“TLS_PSK_WITH_ARIA_128_CBC_SHA256”
“TLS_PSK_WITH_ARIA_128_GCM_SHA256”
“TLS_PSK_WITH_ARIA_256_CBC_SHA384”
“TLS_PSK_WITH_ARIA_256_GCM_SHA384”
“TLS_PSK_WITH_CAMELLIA_128_GCM_SHA256”
“TLS_RSA_PSK_WITH_CAMELLIA_256_CBC_SHA384”
“TLS_DHE_RSA_WITH_AES_128_CCM_8”
“TLS_DHE_RSA_WITH_AES_128_GCM_SHA256”
“TLS_DHE_RSA_WITH_AES_256_CBC_SHA”
“TLS_DHE_RSA_WITH_AES_256_CBC_SHA256”
“TLS_DHE_RSA_WITH_AES_256_CCM”
“TLS_DHE_RSA_WITH_AES_256_CCM_8”
“TLS_DHE_RSA_WITH_ARIA_128_CBC_SHA256”
“TLS_DHE_RSA_WITH_ARIA_128_GCM_SHA256”
“TLS_DH_RSA_WITH_AES_128_CBC_SHA256”
“TLS_DHE_RSA_WITH_CAMELLIA_128_CBC_SHA256”
“TLS_DHE_RSA_WITH_CAMELLIA_256_CBC_SHA256”
“TLS_ECDHE_RSA_WITH_CAMELLIA_256_CBC_SHA384”
“TLS_PSK_WITH_CAMELLIA_128_CBC_SHA256”
“TLS_RSA_PSK_WITH_CHACHA20_POLY1305_SHA256”
“TLS_SRP_SHA_DSS_WITH_3DES_EDE_CBC_SHA”
“TLS_DHE_DSS_WITH_CAMELLIA_128_CBC_SHA”
“TLS_DHE_PSK_WITH_CAMELLIA_256_CBC_SHA384”
“TLS_RSA_WITH_NULL_SHA256”
“TLS_RSA_WITH_NULL_SHA”
“TLS_PSK_WITH_NULL_SHA384”
“TLS_PSK_WITH_NULL_SHA256”
)
$SuitesEnabled = @()
foreach($CSuite in $WeakCiphers){
Foreach ($CS in (Get-TlsCipherSuite -Name $CSuite)) {Disable-TlsCipherSuite -Name $CS.name}
}
Danach verbleiben auf dem System nur noch Cipher Suites die als strong oder recommended eingestuft sind. Unsichere Cipher Suiten dürften auf dem System gar nicht mehr vorhanden sein bzw. unterstützt werden.
Verschlüsselungssuites mit der Powershell verwalten
In diesem Dokument suchen wir nach unsicheren Ciphersuiten, lassen uns die Eigenschaften anzeigen und deaktivieren anschließend die unsicheren Suiten.
Recommended Cipher Suites 2023-2024
Die in dieser Liste empfohlenden Cipher Suiten für TLS v1.2 können bedenkenlos eingesetzt werden.
Die Excelliste enthält ebenso die korrespondierenden OpenSSL Cipher Suites sowie weitere wichtige Details zur Anwendung.